Is the cloud secure?
Cloud adoption has skyrocketed in the last few years and there is a false premise that the cloud is secure. Cloud security is a shared responsibility between your vendor and organization. However, your organization is always responsible for securing your own data which is a misconception to the public. The cloud will give your organization more agility but requires you to be more vigilant and develop a zero trust model. Find out how we can help keep your policy consistent across your organization and in the cloud.
Useful and Effective Tools

You need visibility in the cloud.
You need a firewall in the cloud that has visibility to all your traffic including your internal organization. In our opinion, Palo Alto Networks does this best. With Palo Alto Networks you can apply the same ruleset to your organization's network, cloud, SaaS, and endpoint which is unique compared to other vendors.

You need secure networking in the cloud
Existing network and security architectures are challenged by the application transitions to the public cloud and SaaS environments.
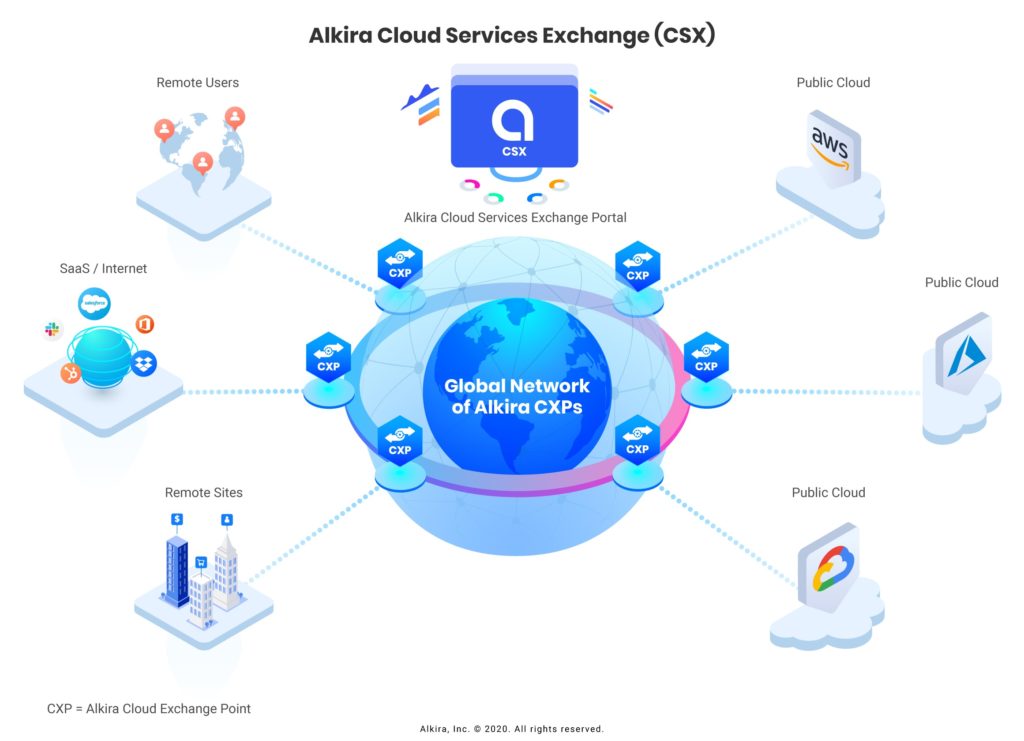
Alkira Cloud Services Exchange™ is a global unified network platform for the cloud era delivered as-a-service. It offers consistent and dramatically simplified networking and security experience for on-premise, cloud, and multi-cloud environments. With Alkira, you leverage digital design canvas to draw your end-to-end network connecting users, sites and clouds with integrated network and security services, operational visibility and governance. The entire network is provisioned in 1-click and ready for use in minutes.
Your network for the cloud has the following main security benefits:
- Instant encrypted multi-region/multi-cloud network transport for strong data privacy
- Uniform Firewall security policy enforcement for on-premise, cloud and multi-cloud application traffic
- Autoscaling (up and down) of Firewall security policy enforcement based on real-time capacity demand
- End-to-end network segmentation
- Full network and network security management, monitoring and troubleshooting